Authored by: Tim Boles
All software systems have degrees of vulnerability, and no single security product can fully safeguard a network from every cyberattack it may face. The question then becomes: what defensive strategy can be put into place that allows systems to detect security vulnerabilities and fend off attackers at the early stages, before severe risk and compromise take place?
At Spinnaker Support, we approach system security through Defense-in-Depth, a six-layer defensive strategy that utilizes the military tactic of leveled fortification rather than a single line of defense. This type of method works to debilitate attackers trying to breach the system at the early stages before they can breach high-risk data and assets. In other words, if one layer is compromised, redundant security layering fortifies the system to continually combat attackers head on.
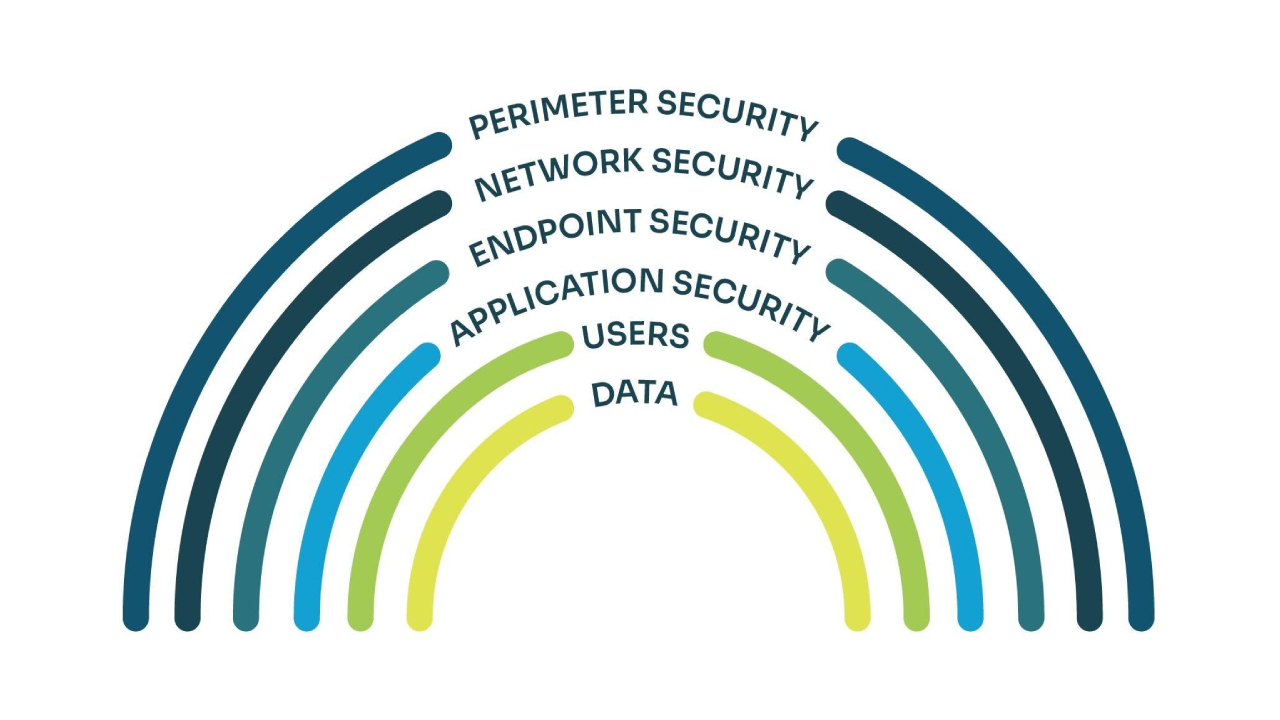
Understanding Security Layers and Levels of Risk
Implementing a Defense-in-Depth strategy begins with a company’s own understanding of their initial lines of defense, which resides in the first three layers of security: Perimeter, Network, and Endpoint.
Teams that have a working knowledge of their policy and governance concerning early defensive tactics (i.e. firewall, VPN, anti-virus, DPL) have a stronger chance to fight off common cyberattack vectors at the onset.
Implementing Defense-in-Depth
At Spinnaker Support, we expertly advise and address our clients’ complexities and risk levels at the inner three layers: Application, Users, and Data.
We evaluate security layers from a Category of Weakness (CWE) level. Evaluation at this level might seem overwhelming since there are over 900 identifiable weaknesses (https://cwe.mitre.org). However, we have the tools and an extensive knowledge base to assess CWEs that are the highest risk to their environment, and work with companies to fortify inner defense layers to create a comprehensive system of defenses.
Defending your Database through Hardening
Designing and configuring a database with security in mind can significantly decrease your exposure to known vulnerabilities. Securing the location, hardware, and data is the first step in creating a secure posture for your system. This will help maintain the confidentiality, integrity, and availability of the data. Isolating and limiting access to your data sources is key to help defend against a potential data breach.
When developing user management policies and procedures implement the Principle of Least Privilege, which limits access to data. Users are granted access to review and manipulate data within the boundaries needed to perform their specific job functions without gaining further access or hindering job performance. Following the Principle of Least Privilege creates a much stronger defense against actors trying to steal or manipulate data stored in your database.
The Principle of Least Privilege is only one hardening technique that Spinnaker Support prescribes to our clients to implement. There are many other areas to consider when hardening a database. As part of our on-boarding process we help our clients harden their systems against benchmarks including CIS Benchmarks, DISA-STIGs, and Oracle documented best practices to name a few.
Patching your database on a routine schedule helps with your security posture but it is paramount to continue hardening not only the database, but the systems that encounter your data. Each point represents an area of entry and will need its own layered compensating controls to secure your technology ecosystem.
Defense-in-Depth for Holistic Protection
Knowing your company’s defenses can go a long way when evaluating the risk of a vulnerability being exploited on your system. The result is a full-scale defense strategy to help security organizations reduce vulnerabilities, stall attack vectors, and mitigate risk of your system being compromised.
For more information, please visit https://www.spinnakersupport.com/third-party-support/security-vulnerability/