Authored by: Tim Boles
This is the second in a series of articles providing an overview of aspects for Oracle database security that are experts believe to be the most efficient, in terms of time, effort and costs to implement. We call these “Quick Wins.”
Implement Least Privileges
Security best practices include limiting user and application privileges to only those needed to perform assigned work. This security best practice is often called the Principle of Least Privileges (PoLP). The idea behind PoLP is to limit a user’s ability to disrupt the database and limit user access to sensitive data. It is well known that many system breaches come from compromised accounts. Adhering to PoLP limits what a cybercriminal can do with a compromised account.
There are four common bad practices that result in users having unnecessary privileges
-
Users are granted SELECT ANY TABLE privilege, which provides them access to all tables, including administrative tables and views.
-
Users are assigned Oracle default roles, like DBA and RESOURCE, which provide capabilities well beyond what is needed for day-to-day work.
-
Users’ privileges are not reassessed when they switch company roles, leaving privileges in place that are not needed in their new role.
-
Users are assigned the privileges of another user without analyzing if the assigned work is the same. This often provides new users privileges beyond their current assignment needs.
A major stumbling block in implementing PoLP is knowing the exact privileges a user needs to perform their work. Oracle Database Enterprise Edition versions newer than 12c include the Privilege Analysis feature. This feature helps enforce the granting of least privileges for users and applications by:
-
Reporting on actual privileges and roles used in the database.
-
Identifying unused privileges and roles by users and applications.
The Privilege Analysis feature has four defined types of analysis it can perform
|
Analysis Type |
Description |
|
G_DATABASE |
Analyzes all used privileges (except those the SYS user employs). |
|
G_ROLE |
Analyzes privileges related to specified roles. |
|
G_CONTEXT |
Analyzes privileges based on a defined condition. |
|
G_ROLE_AND_CONTEXT |
Combines G_ROLE and G_CONTEXT. Analyzes privileges related to specified roles based on a defined condition. |
Access to the Privilege Analysis feature is through the database package DBMS_PRIVILEGE_CAPTURE. There are four steps the administrator must perform through this package when executing a privilege analysis. The steps are described below, and the related procedures are shown in Figure 4.
-
The type of privilege analysis to perform is selected, and a policy is created based on the decision.
-
Based on the user workload, the administrator decides on the start time and enables the policy.
-
When a complete user workload has been captured, the administrator disables the policy.
The administrator generates the results and reviews it for any privileges that need adjustment.
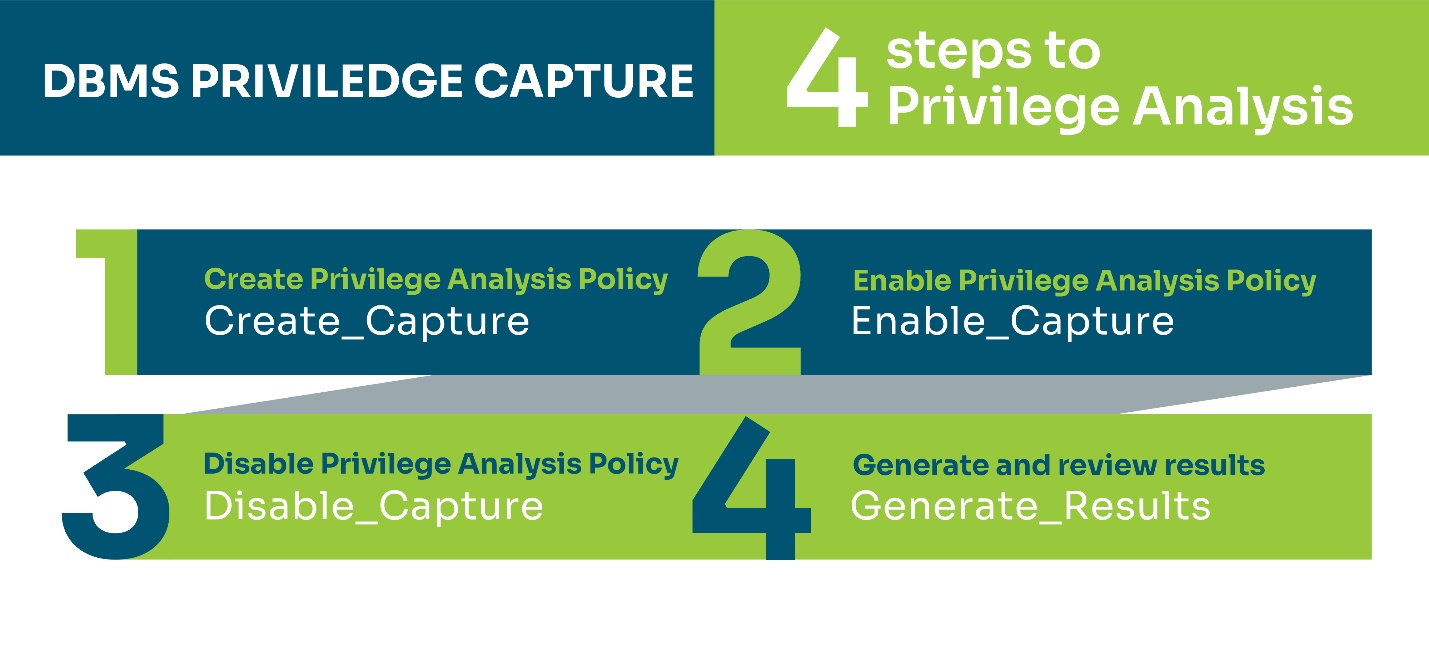
Figure SEQ Figure \* ARABIC 4 : Four steps to privilege analysis
-
Getting a good breadth of captures that span different time periods and system usage would be best to ensure a complete capture of privilege usage. As a best administrative practice, it is advisable to create new roles with the correct privileges and assign the roles to the users. Privilege management is easier when using this method because granting and revoking privileges is then possible through the role and not individual users.
Summary
Implementing the principle of least privilege is an easy, quick way to increase the security posture of your database. As with any database change, there is always some risk, so be sure to test the changes in non-production environments before attempting them in production. At Spinnaker Support, we encourage all organizations to take this initial second step in minimizing the risk of unwanted exposure to your organization’s data.
If you decide to join our client list, you will be provided with a Security Assessment that includes reviewing your system against not only the CIS Benchmarks but also against DISA-STIGs, Oracle Security documentation, and other benchmarks. We will use our findings to guide you in improving your security posture and removing attack vectors that cybercriminals use to attack systems.
For more information, please visit https://www.spinnakersupport.com/third-party-support/security-vulnerability/